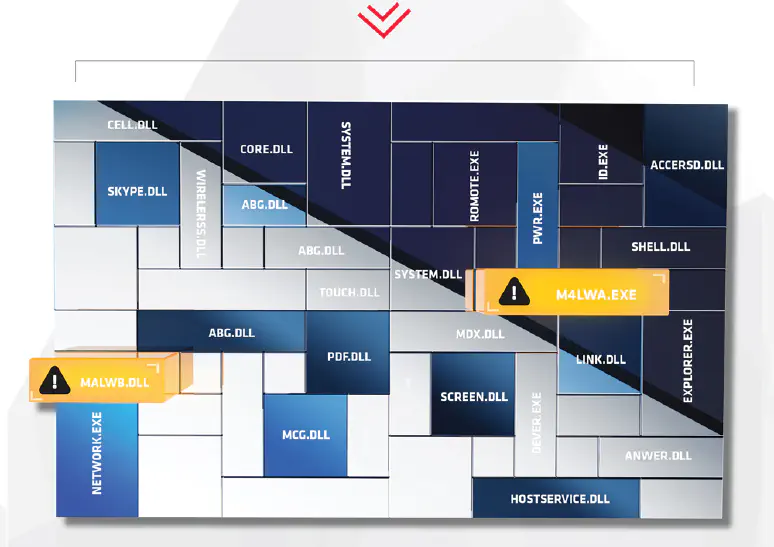
 case studies
case studies
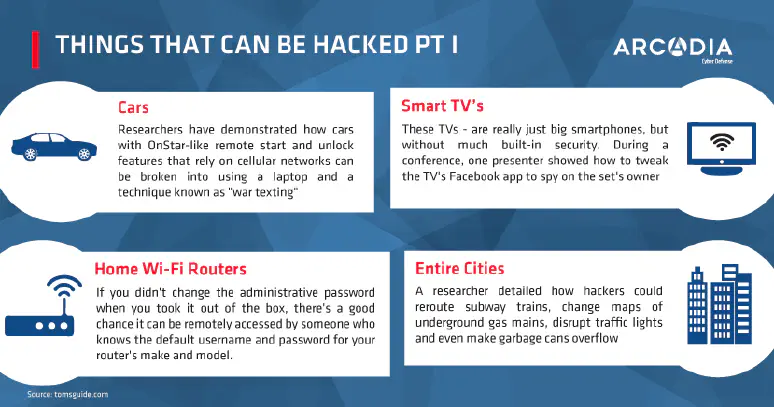
 infographics
infographics
 infographics
infographics
 infographics
infographics
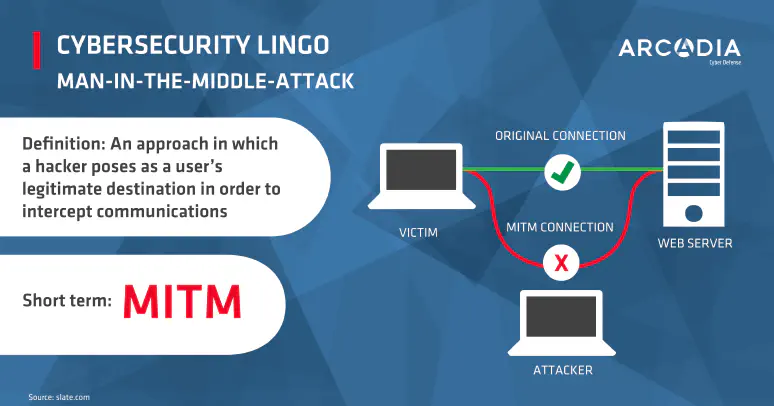
 infographics
infographics
 infographics
infographics
 infographics
infographics
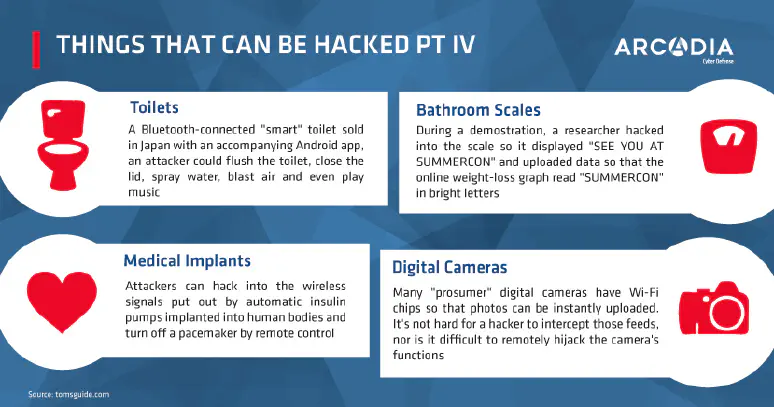
 infographics
infographics
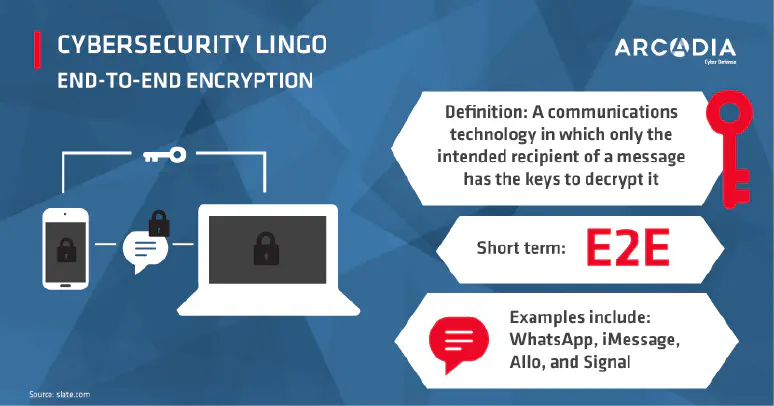 infographics
infographics
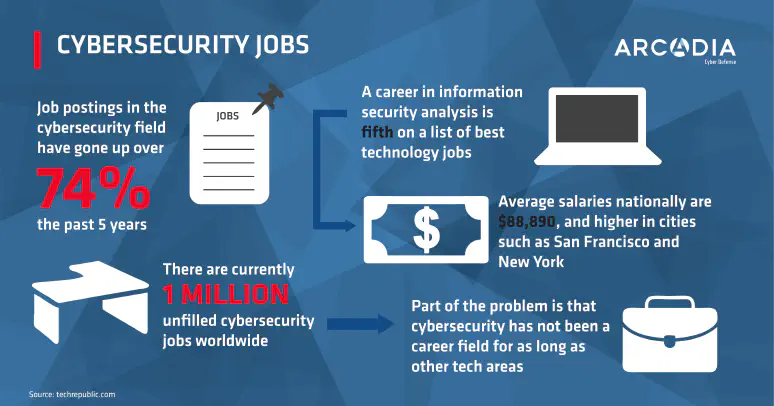 infographics
infographics
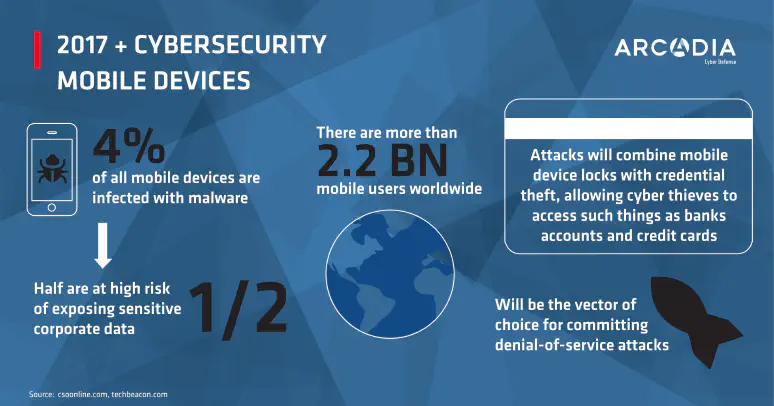 infographics
infographics
 videos
videos
 videos
videos
 videos
videos
 infographics
infographics
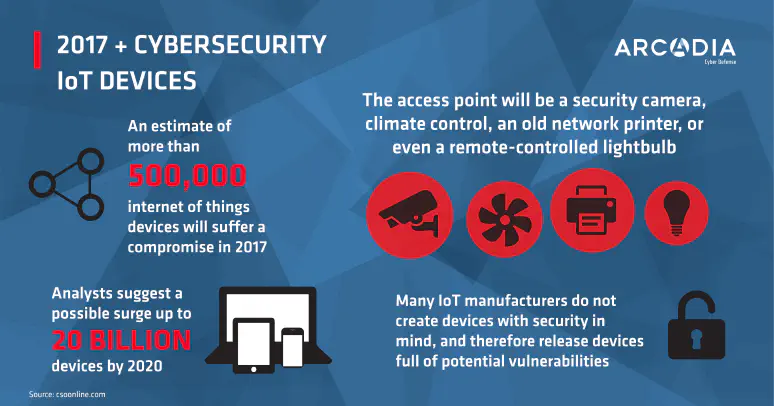 infographics
infographics
 infographics
infographics
 videos
videos
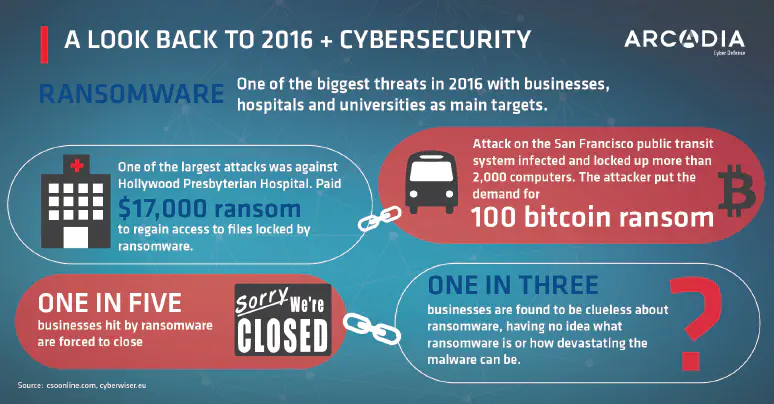 infographics
infographics
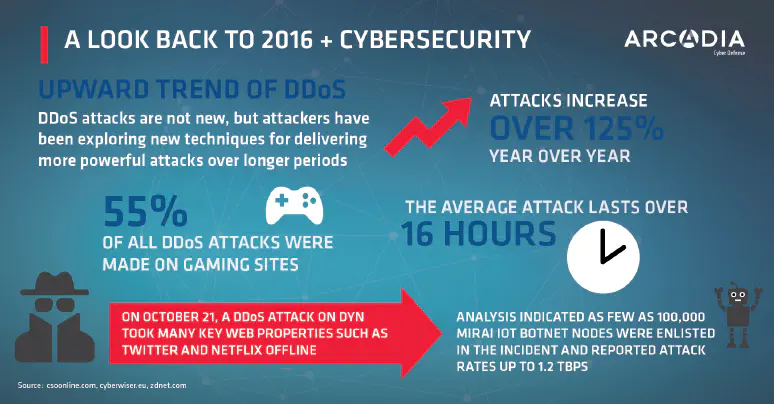 infographics
infographics
 videos
videos
 videos
videos
 data sheets
data sheets
 webinars
webinars
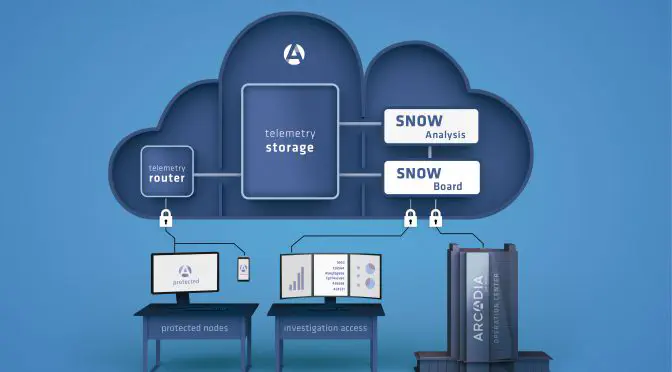 data sheets
data sheets
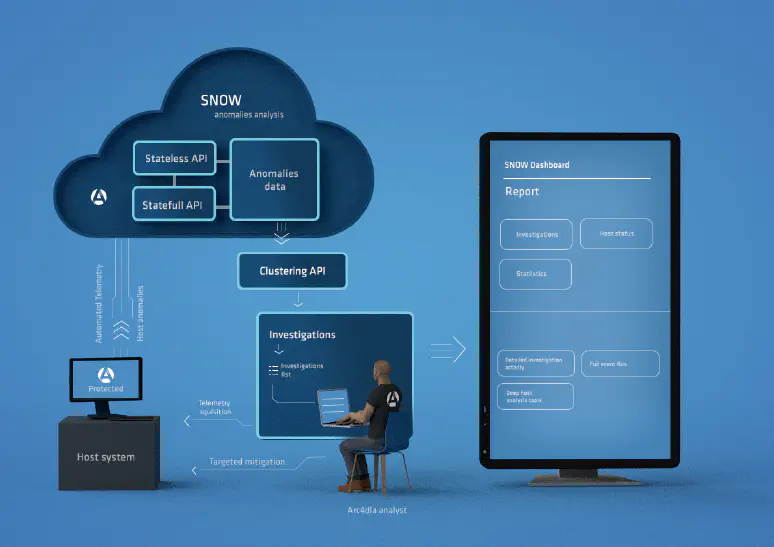 data sheets
data sheets
 webinars
webinars
 data sheets
data sheets
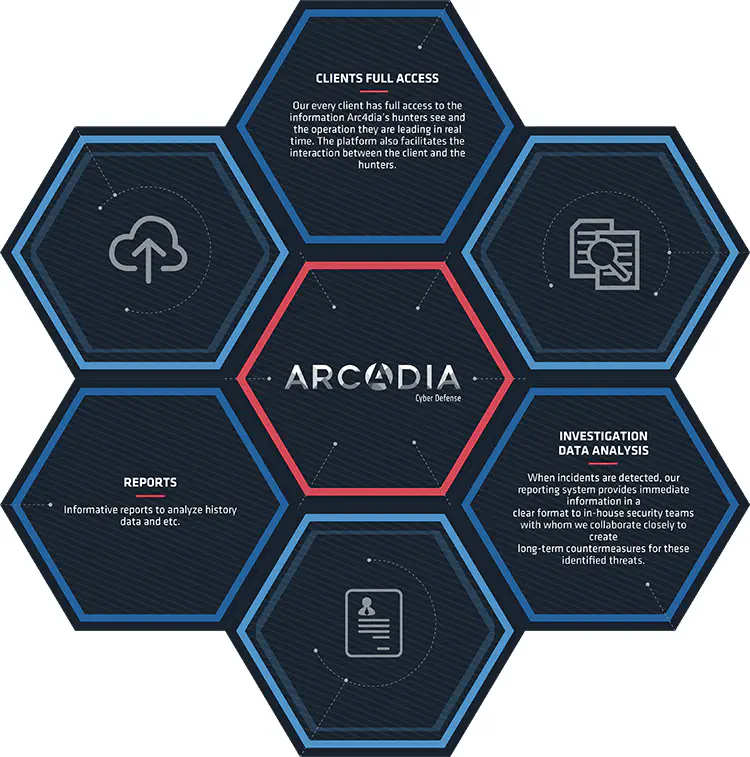 data sheets
data sheets
 videos
videos
 videos
videos
 data sheets
data sheets
 data sheets
data sheets
 courses
courses
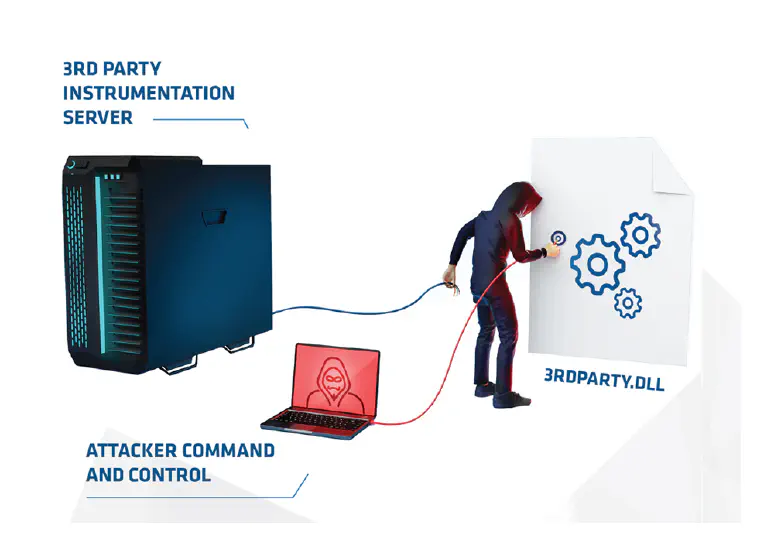 case studies
case studies
 courses
courses
 courses
courses
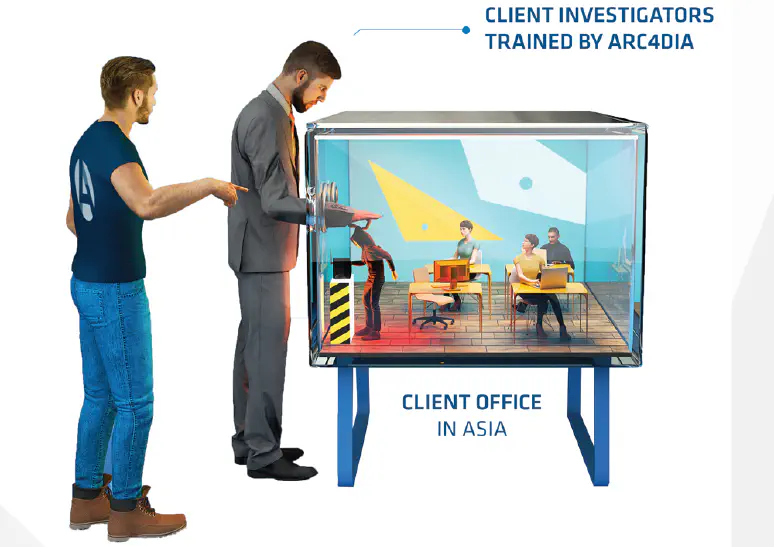 case studies
case studies
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
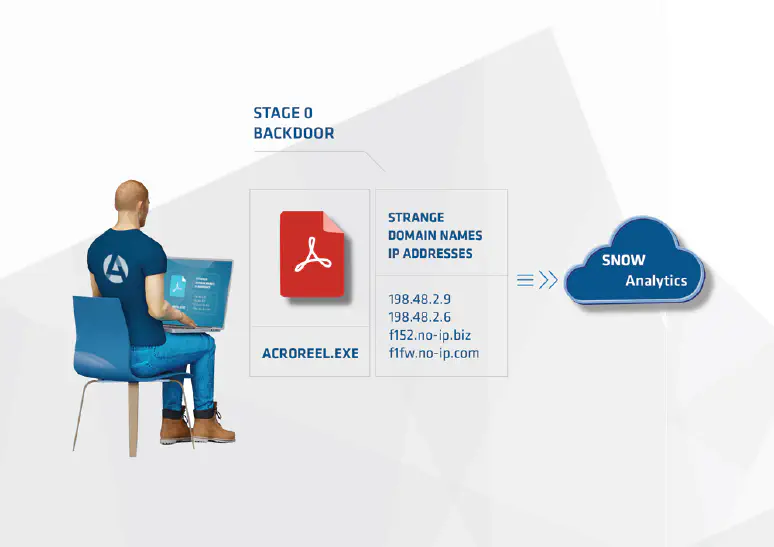 case studies
case studies
 courses
courses
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 videos
videos
 reports
reports
 videos
videos
 reports
reports